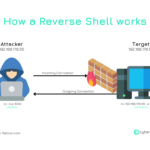
Welcome to the world of the best hacking tools – the ultimate digital arsenal for anyone diving into cybersecurity or ethical hacking. These powerful tools, like Metasploit, Nmap, and Wireshark, are your go-to for scanning networks, uncovering vulnerabilities, and staying one step ahead of potential threats. Whether you’re cracking passwords, probing for weaknesses, or testing website security, these 16 tools represent the cream of the crop in the hacking world. Ready to level up your skills? Let’s get started!
Tools Overview
Metasploit Framework
The Metasploit Framework is a comprehensive tool for developing and executing exploits. It is used to uncover and exploit vulnerabilities in operating systems, networks, and applications. The Metasploit Framework is available as an open-source version (Metasploit Community Edition), with paid versions like Metasploit Pro also available.
Nmap
Nmap is a versatile network scanner used for exploring networks and creating network maps. This tool helps identify open ports and detect vulnerabilities in network configurations. Nmap is open source.
Wireshark
Wireshark is a network protocol analyzer used for monitoring and analyzing network traffic. It helps identify vulnerabilities in network traffic, such as unencrypted data transmission. Wireshark is also open source.
John the Ripper

John the Ripper is a password-cracking tool that identifies weak passwords. It targets weak and easily guessable passwords. John the Ripper is an open-source tool.
Burp Suite
Burp Suite is a platform for testing the security of web applications. It helps identify vulnerabilities such as SQL injections, cross-site scripting (XSS), and cross-site request forgery (CSRF). Burp Suite is available in a paid version (Burp Suite Professional), with a limited free version (Burp Suite Community Edition) also available.
Sqlmap
Sqlmap is a tool that automates the process of detecting and exploiting SQL injection vulnerabilities. It specifically addresses SQL injection vulnerabilities. Sqlmap is an open-source tool.
Nessus

Nessus is a vulnerability scanner that checks networks for security flaws. It helps identify a wide range of network and application vulnerabilities. Nessus is paid software.
Hashcat
Hashcat is a password-cracking tool designed to recover compromised passwords. It targets weak and compromised passwords. Hashcat is open source.
WPScan

WPScan is a security scanner for WordPress websites. It helps uncover vulnerabilities in WordPress plugins, themes, and core installations. WPScan is open source.
Hydra
Hydra is a password-cracking tool that performs brute-force attacks on various protocols. It targets weak passwords on protocols such as HTTP, FTP, and SSH. Hydra is open source.
Wfuzz
Wfuzz is a tool for performing brute-force attacks on web applications. It helps identify vulnerabilities like hidden files and directories, as well as parameter fuzzing. Wfuzz is open source.
Netcat
Netcat is a network utility used for reading and writing data across network connections. It aids in diagnosing network issues and identifying weaknesses in network security configurations. It is often used build reverse shells. Netcat is open source.
Dirbuster
Dirbuster is a brute-force tool aimed at discovering hidden files and directories on web servers. It helps identify vulnerabilities like hidden directories and files that may contain sensitive information. Dirbuster is open source.
Xxser

Xxser is a tool for finding and exploiting cross-site scripting (XSS) vulnerabilities. It specifically addresses XSS vulnerabilities. Xxser is open source.
Nikto
Nikto is a web server scanner that aims to identify security issues and vulnerabilities. It identifies issues such as outdated software, configuration errors, and insecure files. Nikto is open source.
Aircrack-ng
Aircrack-ng is a tool used for testing the security of Wi-Fi networks. It helps identify vulnerabilities like weak encryption and passwords in Wi-Fi networks. Aircrack-ng is open source.
These tools are useful for both professional security researchers and beginners in cybersecurity. They help identify and address various types of vulnerabilities in systems, networks, and applications.