Imagine you have a high-tech security system for your house. The doors are locked with the latest deadbolts, and the windows are fitted with impenetrable bars. But what if someone simply finds the key and lets themselves in? That’s what traditional password security is like: a password is like the key to your digital home—and it can be easily stolen or guessed. That’s where Multi-Factor Authentication (MFA) comes in, adding extra layers of protection to make unauthorized access much more difficult. But what exactly is MFA, and how does it work? Let’s take a deeper dive.
What is Multi-Factor Authentication (MFA)?

Multi-Factor Authentication (MFA) is like a double or triple lock system for your digital life. It ensures that even if someone knows your password, they still can’t access your account without providing additional proof of identity. MFA requires not only a password but also a second (or even third) factor to confirm who you are. These additional factors make it far harder for cybercriminals to gain access.
Imagine you’re creating a new online account. In addition to entering a username and password, you may also need to input a code sent to your smartphone. Or perhaps you’ll be asked to scan your fingerprint or perform a facial recognition scan. All of these steps significantly increase security, ensuring that even if a password is compromised, a second (or third) factor is still needed to gain access.
What’s the Difference Between 2FA and MFA?

You might be wondering about the difference between Two-Factor Authentication (2FA) and Multi-Factor Authentication (MFA). The answer is simple: 2FA is a specific type of MFA that uses exactly two factors. In contrast, MFA can involve more than two factors. While 2FA still offers solid protection, MFA allows for more flexible and stronger security measures.
Example:
- 2FA: You enter your password and then receive a code via SMS.
- MFA: You enter your password, receive a code via SMS, and then scan your fingerprint.
Therefore, MFA is potentially more secure because it adds multiple layers of protection. More layers, less risk.
What is 3-Factor Authentication?
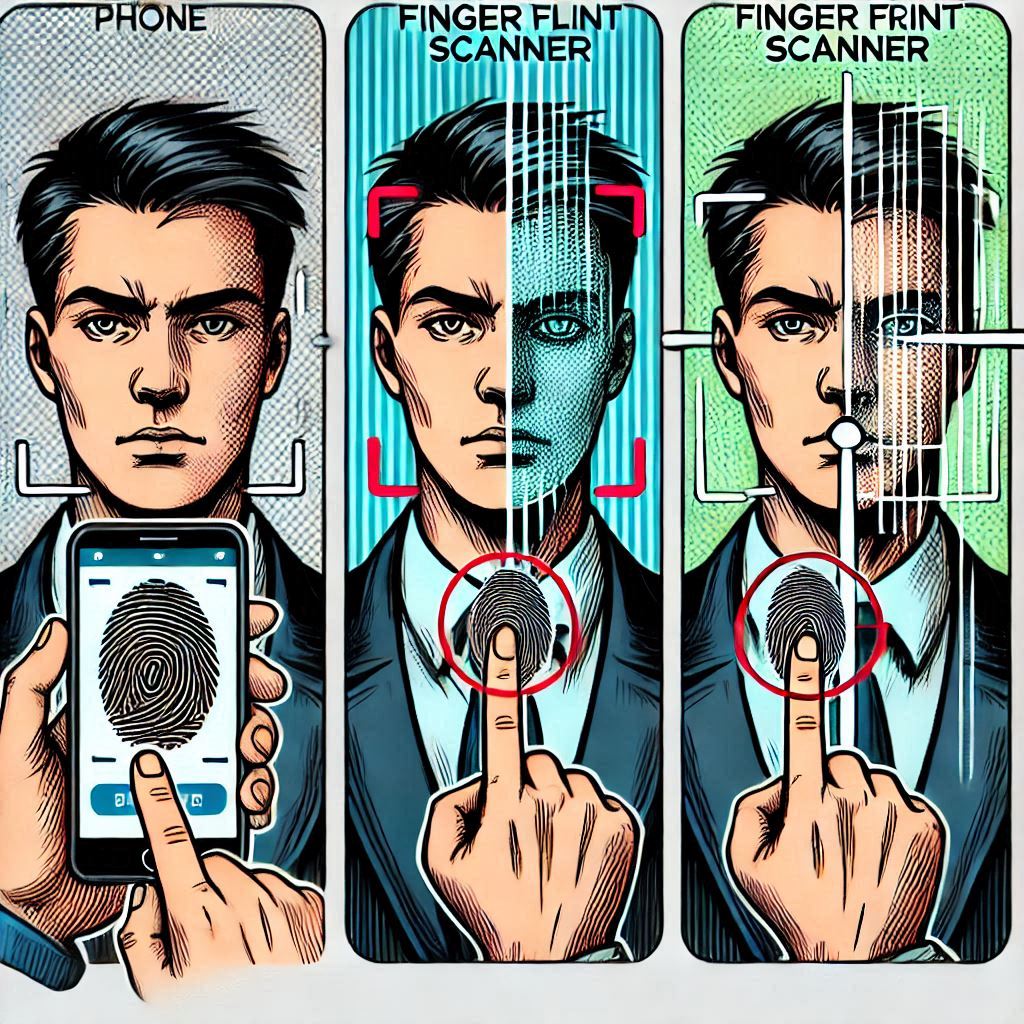
If you thought two factors were secure enough, then 3-Factor Authentication (3FA) is here to take security to the next level. In 3FA, you are required to provide an additional factor on top of your password and a possession factor (e.g., a one-time code), such as a biometric scan.
Example:
- You enter your password (Knowledge factor).
- You receive a code on your smartphone (Possession factor).
- You scan your fingerprint or face (Inherence factor).
3FA is especially useful in highly secure environments—like MFA for online platforms and apps that handle confidential or extremely valuable data.
Why is MFA So Important?

Think of your company like a bank—a place where valuable information and resources are kept. Would you leave the door wide open and just hope no one breaks in? Of course not. The same principle applies to your digital resources. MFA ensures that only those who are authorized can access your data and protects against common security threats like phishing and password theft.
MFA Security Benefits
- Increased Data Security: MFA makes it nearly impossible to access an account with just a password. Even if a password is compromised, another factor is still required to gain access.
- Prevention of Identity Theft: In a world where hackers are constantly looking for stolen credentials, MFA protects your identity.
- Secure Remote Work: Especially in today’s world of working from home, it’s essential to ensure your employees have secure access to company resources. MFA helps ensure this protection.
The Different Authentication Factors

MFA uses three main factors to verify your identity. These factors can be grouped into three broad categories:
- Knowledge Factor (Something you know): A password or PIN is the most common knowledge factor. Unfortunately, this is also the most commonly exploited factor, as passwords are often weak or reused across multiple platforms.
- Possession Factor (Something you have): This could be a one-time code sent to your mobile phone, a hardware token, or an authenticator app.
- Inherence Factor (Something you are): Biometric data such as a fingerprint, facial scan, or voice recognition falls into this category. This factor is particularly secure as it’s nearly impossible to duplicate.
What is the Strongest Authentication Factor?
Among the three main factors, the Inherence Factor is the strongest. Biometric MFA methods like fingerprint scanning or facial recognition provide the highest level of security, as they are unique to you. A password or code can be stolen, but your fingerprint or face can’t be copied easily.
MFA for Businesses and the Importance of Compliance
For businesses, especially those dealing with sensitive data (like in the healthcare industry or IAM solutions with MFA integration), MFA is critical. Achieving compliance with MFA (e.g., GDPR, HIPAA) ensures your security measures align with regulatory requirements and protects your company from fines and reputational damage.
- MFA for Small Businesses: Small businesses can also benefit from the additional security MFA offers. For smaller companies, it can be harder to implement a full security infrastructure, but using MFA can significantly improve the protection of customer and business data.
- MFA for IT Administrators: The IT department plays a crucial role in implementing and managing MFA. They need to ensure the right authentication factors are selected and regularly reviewed for all users and systems. A solid MFA implementation strategy helps close security gaps and protects your business from cyber threats.
Adaptive MFA and Risk-Based Authentication

MFA doesn’t always have to be rigid and inflexible. Adaptive MFA is an intelligent system that dynamically decides which authentication steps are needed based on the risk level of the access attempt. If someone is logging in from a secure network, the MFA check might be minimal. However, if unusual login activity is detected, the system might request additional authentication factors.
Risk-based authentication is another development that allows companies to adjust security policies based on user behavior and the specific circumstances of access. This type of MFA helps ensure that you don’t have to go through the same authentication process every time while maintaining a high level of security.
Passwordless Authentication: The Future of MFA?

Another exciting trend in MFA is the move toward passwordless authentication. With this method, no passwords are required to verify identity. Instead, biometric features or other possession factors are used. This has two advantages: First, it eliminates the risk of password theft, and second, it makes the login process faster and more convenient.
One-Time Passwords (OTPs) and Push Notifications are common technologies used to provide seamless and secure authentication. These methods offer a convenient way to log in to applications and platforms securely.
What is the Biggest Drawback of Two-Factor Authentication?

While Two-Factor Authentication (2FA) offers many benefits, it does have some downsides. The biggest drawback? It’s not foolproof. While 2FA offers more protection than just a password, there are still security gaps, especially when using SMS-based codes that can be intercepted. Additionally, the effectiveness of 2FA depends on the strength of the possession factor used—if it’s weak, the protection can be compromised.
However, MFA has the answer. By using more secure hardware tokens for MFA security and biometric MFA methods, these vulnerabilities can be avoided, providing a much higher level of protection.
MFA for Consumers: Why Everyone Needs It

It’s not just businesses that need MFA—consumers should use it for their own accounts too. Think about all the online services we use today—social media, email, banking. All of these accounts are potential targets for hackers.
By enabling MFA for online platforms and apps, you make it much harder for attackers to access your sensitive data. For example, if you log into your banking app, MFA can ensure that only you can access your account, even if someone knows your password. This doesn’t just protect your money; it also protects your personal data and digital identity.
Which Free Authenticator App is the Best?

If you’re just getting started with MFA, one of the first questions you might have is, “Which free authenticator app is the best?” There are several options, but some of the most popular and reliable apps include:
- Google Authenticator: Easy to use and widely accepted. It offers a simple way to generate one-time passwords without needing an internet connection.
- Authy: This app provides similar features to Google Authenticator but with the added benefit of storing your codes in the cloud, so you can recover them if you lose your device.
- Microsoft Authenticator: Particularly useful for Windows users, it also supports passwordless logins.
Conclusion: MFA – The Key to Digital Security
Multi-Factor Authentication is more than just a trend—it’s a necessity to protect your digital accounts from hackers. You should never rely solely on the security of your password, and MFA ensures that even if a password is compromised, your account remains safe.
Whether for small businesses, consumers, or IT administrators, MFA for cybersecurity is an essential tool in the arsenal of anyone who wants to protect their data. With the introduction of biometric MFA methods, adaptive MFA, and the possibility of passwordless authentication, security is becoming both safer and more user-friendly. Ultimately, it’s about creating a robust defense that makes unauthorized access to your data as difficult as possible—and MFA is the key to that protection.
Embrace MFA, protect your data, and sleep soundly.