In today’s digital landscape, where cloud services like Microsoft 365, Google Workspace, Salesforce, and AWS are integral to business operations, organizations face a critical challenge: How can they effectively protect data, users, and applications in the cloud without compromising productivity? This is where the Cloud Access Security Broker (CASB) comes into play.
A CASB serves as a security intermediary between users and cloud services, providing visibility, control, and protection for all cloud activities. It is an indispensable tool for modern IT security strategies.

What Is a CASB?
A Cloud Access Security Broker (CASB) is a security solution positioned between an organization’s on-premises infrastructure and cloud service providers. It enforces security policies, monitors data flows, and detects threats, assisting organizations in maintaining compliance and preventing data breaches.
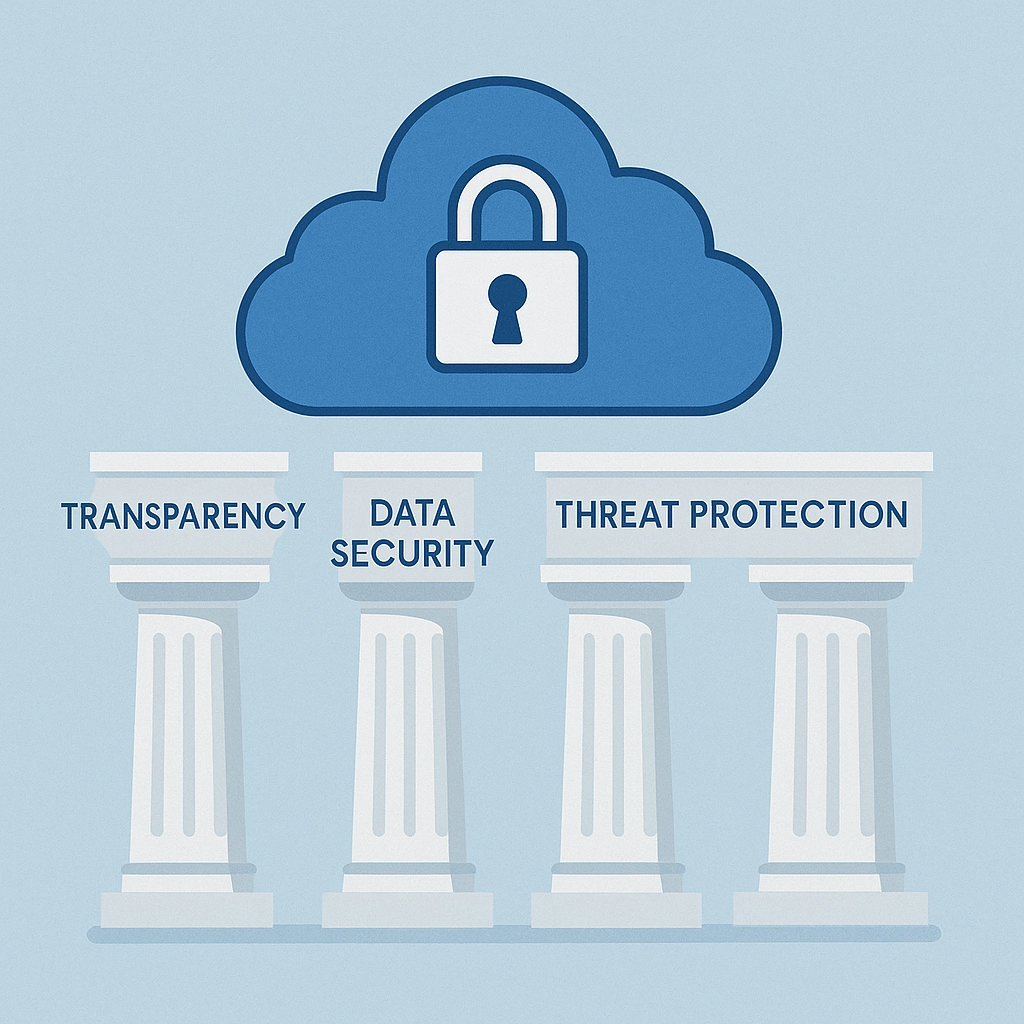
The Four Pillars of a CASB
1. Transparency
CASBs offer comprehensive insights into the usage of cloud services, identifying both authorized and unauthorized applications (shadow IT) and analyzing user behavior. This enables organizations to detect risks early and take appropriate actions.
2. Data Security
Through features like encryption, tokenization, and Data Loss Prevention (DLP), CASBs protect sensitive corporate data. They prevent unauthorized data transfers and ensure that confidential information does not fall into the wrong hands.
3. Threat Protection
CASBs utilize advanced technologies such as machine learning and behavioral analytics to detect anomalies and malicious activities. They provide protection against malware, account hijacking, and other cyber threats. Continuous monitoring of cloud activities helps organizations proactively defend against potential security risks.
4. Compliance
CASBs assist organizations in adhering to legal and regulatory requirements such as GDPR, HIPAA, or PCI-DSS. They offer functionalities for monitoring and auditing cloud activities, managing data residency, and generating compliance reports.
CASB Deployment Models
Depending on specific organizational requirements, CASBs can be implemented in various ways:
API-Based: Direct integration with cloud services without redirecting traffic.
Proxy-Based: Routes traffic through the CASB to provide real-time protection.
Agent-Based: Installs software on endpoints to enforce security policies.
Hybrid Model: Combines different approaches for maximum flexibility and security.
Practical Use Cases
Detecting Shadow IT
CASBs identify unauthorized cloud applications used by employees, enabling organizations to control or block them.
Protecting Sensitive Data
With DLP functionalities, CASBs prevent confidential information from being shared or transferred without authorization.
Access Control
CASBs allow organizations to control access to cloud services based on user identity, location, or device type.
Compliance Reporting
They provide detailed reports and audit logs to demonstrate compliance with regulations.
Conclusion: CASB as an Essential Component of Cloud Security Strategy
In an increasingly cloud-based work environment, CASBs are central to ensuring security, compliance, and efficiency. They offer comprehensive control over cloud activities, protect sensitive data, and assist organizations in meeting legal requirements. By properly implementing a CASB, organizations can fully leverage the benefits of the cloud without compromising security.