In the ever-evolving landscape of web security, protecting your web applications from vulnerabilities is paramount. One of the most persistent and dangerous threats is Cross-Site Scripting (XSS). This comprehensive guide will explore how to use XSStrike, a powerful tool for identifying and exploiting XSS vulnerabilities, to fortify your web applications against malicious attacks.

Importance of Web Security
Web security is crucial in safeguarding user data, maintaining trust, and ensuring the smooth operation of online services. With the increasing sophistication of cyber threats, implementing robust security measures is not just optional but essential. Neglecting web security can lead to severe consequences, including data breaches, financial losses, and damage to reputation.

Overview of XSS Vulnerabilities
XSS vulnerabilities allow attackers to inject malicious scripts into web pages viewed by unsuspecting users. These scripts can perform unauthorized actions such as stealing cookies, hijacking sessions, and redirecting users to malicious sites. Understanding XSS vulnerabilities is the first step in defending against them. There are three main types of XSS: Stored, Reflected, and DOM-based, each with unique attack vectors and impacts.

Introduction to XSStrike
XSStrike is a cutting-edge open-source tool designed to identify and exploit XSS vulnerabilities in web applications. It stands out due to its advanced scanning techniques and payload crafting capabilities. By automating the detection and exploitation process, XSStrike helps security professionals and developers pinpoint and address XSS vulnerabilities efficiently.

Getting Started with XSStrike
What is XSStrike?
XSStrike is an open-source XSS vulnerability scanner and exploitation suite. It is built with a variety of features that make it an indispensable tool for security testing. Its ability to craft intelligent payloads and perform thorough scans distinguishes it from other tools in the market.
Features of XSStrike
XSStrike comes equipped with a multitude of features, including automatic payload encoding, support for multiple payload types, fuzzing capabilities, and integration with other web security testing frameworks. These features enable comprehensive vulnerability assessments, making XSStrike a versatile and powerful tool.
System Requirements
To use XSStrike, ensure your system meets the following requirements: Python 3.6 or higher, a compatible operating system (Windows, Linux, or macOS), and internet access for fetching dependencies. Adequate system resources will ensure smooth operation and efficient scanning.
Installation Guide
Installing XSStrike is straightforward. Open your terminal and execute the following commands:
git clone https://github.com/s0md3v/XSStrike.git
cd XSStrike
pip install -r requirements.txtThis process clones the XSStrike repository and installs all necessary dependencies, setting the stage for effective security testing.
Important: It might be possible that you have to use –break-system-packages or setup a virtual environment.

Understanding XSS Vulnerabilities
Types of XSS Attacks
XSS attacks can be classified into three types:
- Stored XSS attack: Malicious scripts are permanently stored on the target server, such as in a database, and executed when a user accesses the affected content.
- Reflected XSS attack: Malicious scripts are reflected off a web application onto the user’s browser, typically through a URL parameter.
- DOM-based XSS attack: The attack is executed within the Document Object Model (DOM) of the browser, altering the client-side code.
How XSS Exploits Work
XSS exploits involve injecting malicious code into web applications. When users interact with the compromised application, their browsers execute the malicious script, leading to unauthorized actions like data theft, session hijacking, or defacement.
Real-World Examples of XSS Attacks
Notable XSS attacks include the Samy worm on MySpace, which propagated by exploiting a Stored XSS vulnerability, and the Reflected XSS attack on Twitter, which allowed attackers to execute arbitrary JavaScript code in users’ browsers. These examples underscore the critical need for effective XSS mitigation strategies.
The Impact of XSS Vulnerabilities
The impact of XSS vulnerabilities can be devastating. They can compromise user data, damage a company’s reputation, and result in legal and financial penalties. Understanding their impact emphasises the importance of rigorous security testing and proactive vulnerability management.

XSStrike Basics
Interface Overview
XSStrike features a user-friendly command-line interface (CLI) that simplifies the process of scanning and exploiting XSS vulnerabilities. The interface provides clear commands and options, allowing users to customize their scans and payloads effectively.
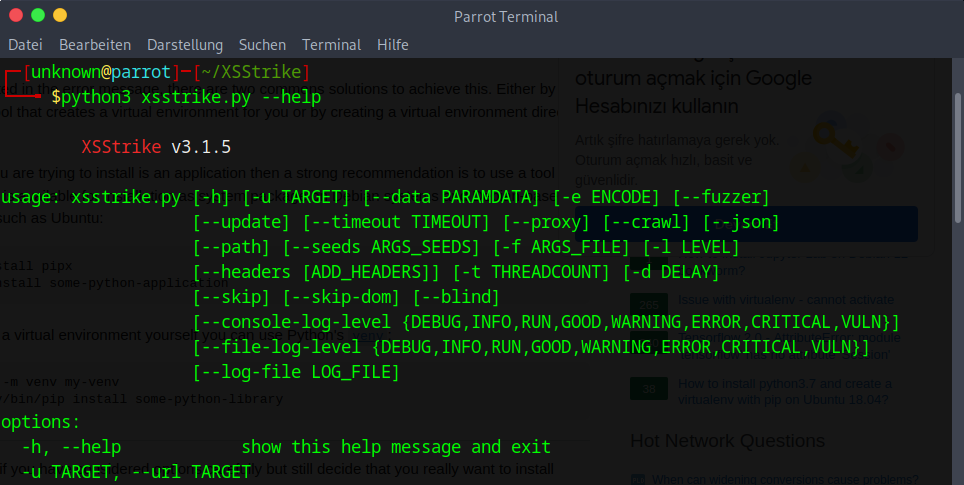
Command-Line Basics
Mastering the command-line interface is crucial for utilizing XSSStrike to its full potential. Basic commands allow you to specify target URLs, select scan types, and configure payload options. Familiarity with these commands enhances your ability to perform precise and efficient security assessments.
Key Commands and Options
Essential commands in XSStrike include:
--url: Specifies the target URL for the scan.--crawl: Enables crawling to discover additional URLs within the target application.--fuzz: Initiates fuzzing to identify potential injection points. Understanding these commands is vital for conducting thorough and effective scans.

Running Your First Scan
Preparing for the Scan
Before initiating a scan, gather information about the target application, including input fields and potential injection points. A thorough preparation phase ensures a comprehensive and effective scanning process.
Target Selection
Choose your target carefully, ensuring it is a legitimate target for security testing. Unauthorized testing can have legal implications, so always obtain proper permissions before conducting security assessments.
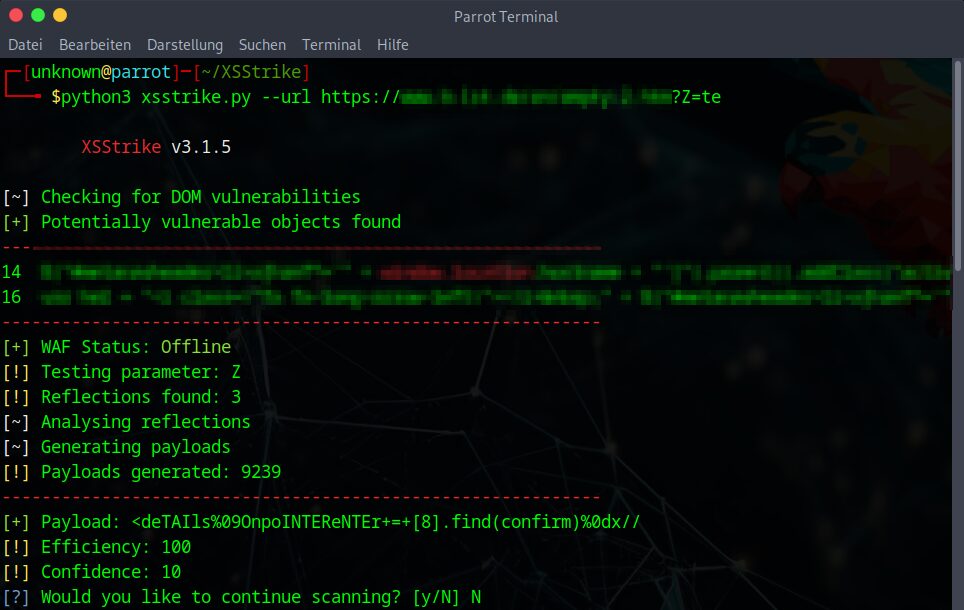
Basic Scan Command
To start a basic scan, use the following command:
python xsstrike.py --url <target_url>This command initiates a preliminary scan of the specified target URL, identifying potential XSS vulnerabilities.
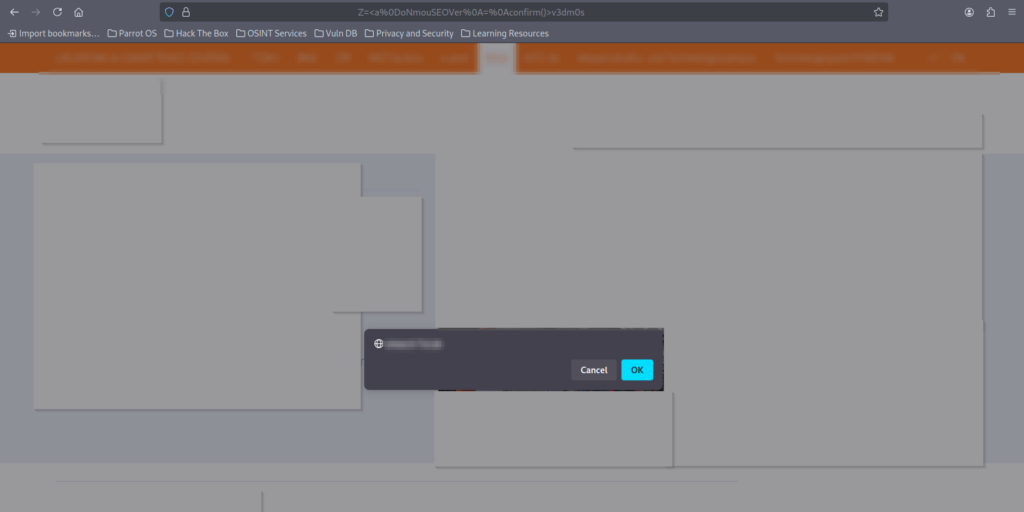
Verify Result
Using the Payload outputed by XSStrike in the browser shows that it worked.
Conclusion
Throughout this guide, we have explored the importance of web security, the nature of XSS vulnerabilities, and how to use XSStrike to identify and exploit these vulnerabilities. By following the steps outlined, you can enhance your web application’s security posture and protect it from malicious attacks.
Web security is an ever-evolving field. Continuous learning and staying updated with the latest security trends and tools are essential for maintaining robust security defenses. Engage with the cybersecurity community, attend workshops, and keep exploring new tools and techniques.
Protecting your web applications from XSS vulnerabilities is a critical component of a comprehensive security strategy. By leveraging tools like XSStrike and adhering to best practices, you can significantly reduce the risk of XSS attacks and ensure a secure and trustworthy user experience.