Choosing the right security solution can make the difference between success and failure when it comes to defending against cyber attacks. From Managed Detection and Response (MDR) to Extended Detection and Response (XDR) and Network Detection and Response (NDR) – each of these solutions has its own strengths and challenges. In this article, we look at the special features and possible applications of MDR, MSSP, EDR, XDR and NDR to help you find the right solution for your security requirements.
Table of Content
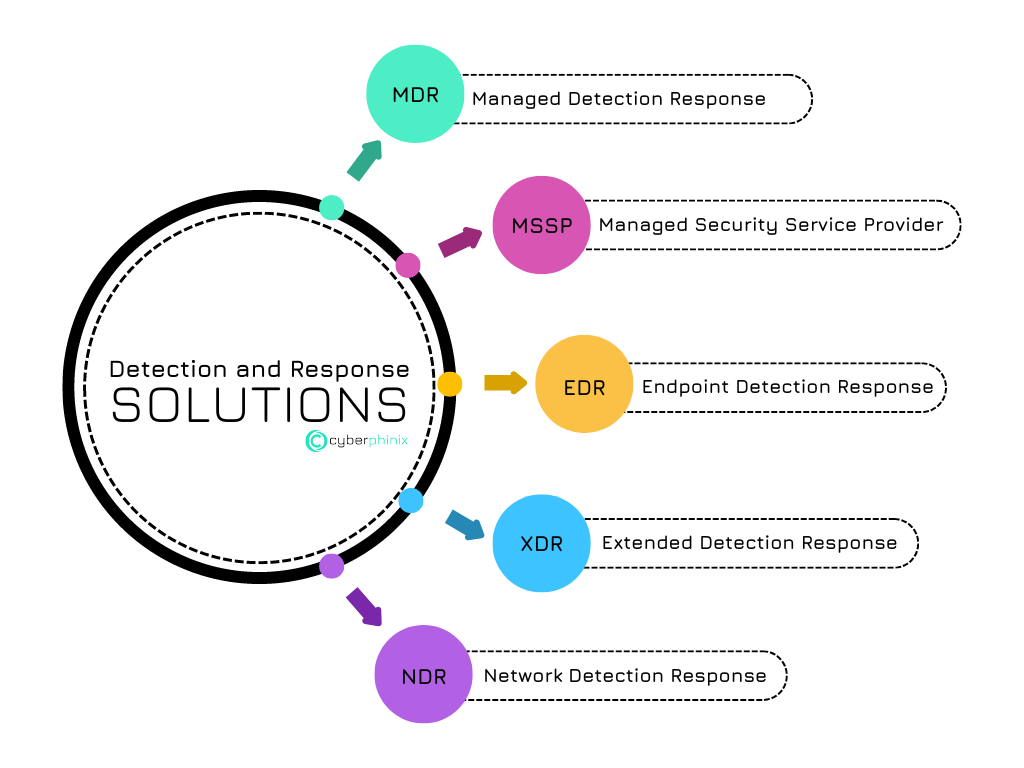
Managed Detection and Response (MDR)

MDR services provide comprehensive security monitoring by an external team of specialists. These services combine advanced technologies with human expertise to detect, analyze and respond to threats in real time. MDR typically includes threat hunting, incident management and forensics.
Use cases
Detection of complex threats: Particularly effective in identifying and combating sophisticated threats such as APTs (Advanced Persistent Threats).
Rapid incident response: Providing a team that can quickly respond to and manage security incidents.
Continuous threat hunting: Proactively search for hidden threats that may be missed by traditional security solutions.
Advantages and disadvantages
Advantages
- Proactive detection: Early identification through continuous monitoring.
- Specialized knowledge: Access to an experienced team of security experts.
- Relief for the internal team: Reduction of the burden on internal IT resources.
Disadvantages
- Costs: Higher running costs compared to internal solutions.
- Dependence: Dependence on the performance and responsiveness of the external service provider.
Managed Security Service Providers (MSSP)

MSSPs offer a wide range of security services, including network monitoring, vulnerability management and compliance management. They enhance an organization’s internal security capabilities and provide continuous monitoring and management.
Use cases
24/7 security monitoring: round-the-clock monitoring for companies that do not have an internal Security Operations Center (SOC).
Compliance management: Support for compliance with regulations and security standards.
Vulnerability management: Regular scans and patches to ensure the security of systems.
Advantages and disadvantages
Advantages
- Comprehensive security solutions: Coverage of many security aspects.
- Scalability: Adaptation of services to the needs of the company.
- Cost efficiency: Often more cost-effective than setting up your own security team.
Disadvantages
- Standardized services: May not be tailored to specific needs.
- Response time: Less specialized and rapid response to specific threats.
Endpoint Detection and Response (EDR)

EDR solutions focus on monitoring and defending against threats on endpoints such as laptops and desktops. EDR tools provide detailed insights into endpoint activity and enable a rapid response to security incidents.
Use cases
Protection against ransomware: Early detection and containment of ransomware attacks by monitoring the end device.
Insider threats: Detection and investigation of suspicious activity from internal users.
Rapid response: Immediate action to eliminate threats on end devices.
Advantages and disadvantages
Advantages
- Specific endpoint security: Targeted security measures for end devices.
- Real-time monitoring: Rapid identification and response to threats.
- Behavior-based analysis: Use of behavioral analysis to detect attacks.
Disadvantages
- Limited coverage: Focuses only on endpoints, not network or cloud resources.
- Management complexity: Can be complex to implement and manage.
Extended Detection and Response (XDR)

XDR extends the capabilities of EDR by integrating data from multiple security controls – such as networks, endpoints and cloud environments. XDR provides an integrated security solution that enables more comprehensive threat detection and response.
Use cases
Unified threat detection: Integration of security data from multiple sources for a more complete threat picture.
Coordinated response: Coordinate responses to threats that affect multiple security domains.
Comprehensive view: Complete monitoring and response across all security domains.
Advantages and disadvantages
Advantages
- Integrated view: Consolidation of data from different sources for comprehensive threat detection.
- Coordinated responses: Better coordination and response to complex threats.
- Advanced analysis: Use of advanced analysis methods to detect and combat threats.
Disadvantages
- Costs: Higher costs due to extended functionalities and integrations.
- Complexity: Complex implementation and management due to the large number of integrated systems.
Network Detection and Response (NDR)

NDR focuses on monitoring and securing the network by analyzing network traffic and detecting anomalies. This solution provides insight into network activity and enables comprehensive detection and response to threats within the network.
Use cases
Detection of network threats: Identifying and responding to threats moving around the network or intruding from the outside.
Network monitoring: Monitoring all network traffic for unusual patterns or suspicious activity.
Detection of lateral movement behavior: Detection of movement within the network that may indicate an ongoing attack.
Advantages and disadvantages
Advantages
- Holistic network monitoring: Comprehensive monitoring of network traffic to detect threats.
- Anomaly detection: Identification of unusual activities that could indicate attacks.
- Network protection: Protection against threats that operate or spread in the network.
Disadvantages
- Complexity of implementation: Integration and management requirements can be high.
- Costs: Can be expensive, especially for extensive networks.
Comparison of Security Solutions

MDR offers specialized, proactive monitoring and response to threats by external experts, while MSSP offers a broader range of security services, but often less specialized response capabilities.
MDR provides comprehensive response and threat hunting by an external team, whereas EDR focuses on endpoint detection and response. EDR is often a subset of MDR functionality.
MDR focuses on specific threat monitoring and response by experts, while XDR offers an integrated solution that covers multiple security areas, providing a more comprehensive view of threats.
MDR provides comprehensive security services and responses, while NDR is specifically designed to monitor and secure the network. NDR is particularly useful for detecting threats in network traffic.
MSSP offers a wide range of security services, including network and endpoint protection, while EDR focuses on detailed endpoint security. MSSP is more comprehensive but less specialized in endpoint monitoring.
MSSP offers versatile security services, while XDR provides an integrated solution for comprehensive threat detection across multiple security domains. XDR can enable deeper analysis and response.
MSSP provides general security monitoring, while NDR is specifically focused on network monitoring and protection. NDR is more specifically focused on network security aspects.
EDR focuses on endpoint security, while XDR provides an advanced solution that integrates data from multiple security controls to enable more comprehensive threat detection.
EDR offers detailed protection and monitoring for end devices, while NDR focuses on network monitoring. Both solutions are complementary, but cover different areas of security.
XDR offers an integrated security solution that combines data from multiple areas, while NDR is specifically aimed at monitoring and securing the network. XDR offers a more comprehensive view, NDR is more specifically focused on network security.
Practical example
Imagine a mid-sized company looking to improve its security strategy. It could choose MDR to receive proactive threat detection and response services from external experts. At the same time, it could use EDR to provide in-depth protection and monitoring for its endpoints. For an integrated security solution, the company could also invest in XDR to get a more comprehensive view of its overall security posture, while NDR covers specific network monitoring needs.
List of requirements for the selection of security solutions
This list provides a comprehensive overview of the various factors that should be considered when selecting a security solution. The exact weighting of each requirement may vary depending on the specific needs and priorities of the organization.
Purpose and objective
- Threat detection: What are the main objectives of the security solution (e.g. malware detection, data loss, internal threats)?
- Response capabilities: How quickly and effectively can the solution respond to security incidents?
Compatibility and integration
- Infrastructure compatibility: How well can the solution be integrated into existing systems and networks (e.g. IT environment, cloud services)?
- Interfaces: Does the solution have APIs or integrations to other security and IT systems?
Scalability
- Growth requirements: Can the solution scale as the organization grows and changes (e.g. increased number of endpoints, network complexity)?
- Performance adaptation: How well does the solution adapt to different performance requirements?
Costs and budget
- Acquisition costs: What are the initial costs associated with implementation?
- Ongoing costs: What are the recurring costs (e.g. maintenance, licenses, support)?
- Cost-benefit ratio: Does the solution offer a good balance between costs and the functions and security gains offered?
Detection and protection mechanisms
- Detection rate: How effective is the solution at detecting threats (e.g. false positive/false negative rates)?
- Behavioral analysis: Does the solution provide in-depth analysis of user and network behavior?
Response and recovery capabilities
- Automation: How well can the solution automatically respond to incidents (e.g. threat isolation, attacker blocking)?
- Recovery: How does the solution support post-incident recovery (e.g. system recovery, data recovery)?
Ease of use and management
- Ease of use: How intuitive is the user interface and management of the solution?
- Training requirements: How much training is required to use the solution effectively?
Compliance and regulation
- Compliance requirements: Does the solution meet relevant regulatory and industry compliance requirements (e.g. GDPR, HIPAA)?
- Audit functions: What audit and reporting features does the solution provide?
Support and service
- Technical support: What type of support does the provider offer (e.g. 24/7 support, technical advice)?
- Service Level Agreements (SLAs): What are the guarantees and commitments regarding availability and support?
Flexibility and adaptability
- Configuration options: How flexibly can the solution be adapted to specific needs and threat scenarios?
- Updates and patches: How regularly are updates provided and how easy is it?
Summary
Choosing the right security solution depends heavily on your company’s specific needs and security posture. While MDR and MSSP offer comprehensive security services, EDR, XDR and NDR focus on specific areas such as endpoints, integrated security and network monitoring. An informed decision should be based on a detailed analysis of your security requirements and the strengths of the different solutions.




