Passwords are like keys to a safe. But what if an attacker doesn’t look for the right key, but simply tries every possible one? Welcome to the world of brute force attacks. In this article, we take a look at what exactly is behind them, how hackers use this technique and how you can effectively protect yourself against them.

What is a brute force attack?
A brute force attack is a method in which an attacker automatically tries different character combinations to crack a password or other authentication mechanism. Either all possible combinations are tried (classic brute force attack) or specific password lists (dictionary attack) are used.

Types of brute force attacks
1. Classic brute force attack
Here, all possible combinations are tried until the correct password is found. This method is particularly effective when weak passwords are used.
2. Dictionary attack
Instead of trying out random combinations, the attacker uses a list of frequently used passwords (e.g. “123456”, “password”).
3. Reverse Brute-Force
Here the attacker takes the opposite approach: he already has a password and tests it with different usernames.
4. Credential Stuffing
This involves using stolen access data from data leaks to log in to other services. As many people use the same password for different accounts, such attacks are often successful.
5. Hybrid Brute-Force
This method combines a dictionary attack with random characters. Example: The attacker tries out common passwords and adds random numbers or special characters.

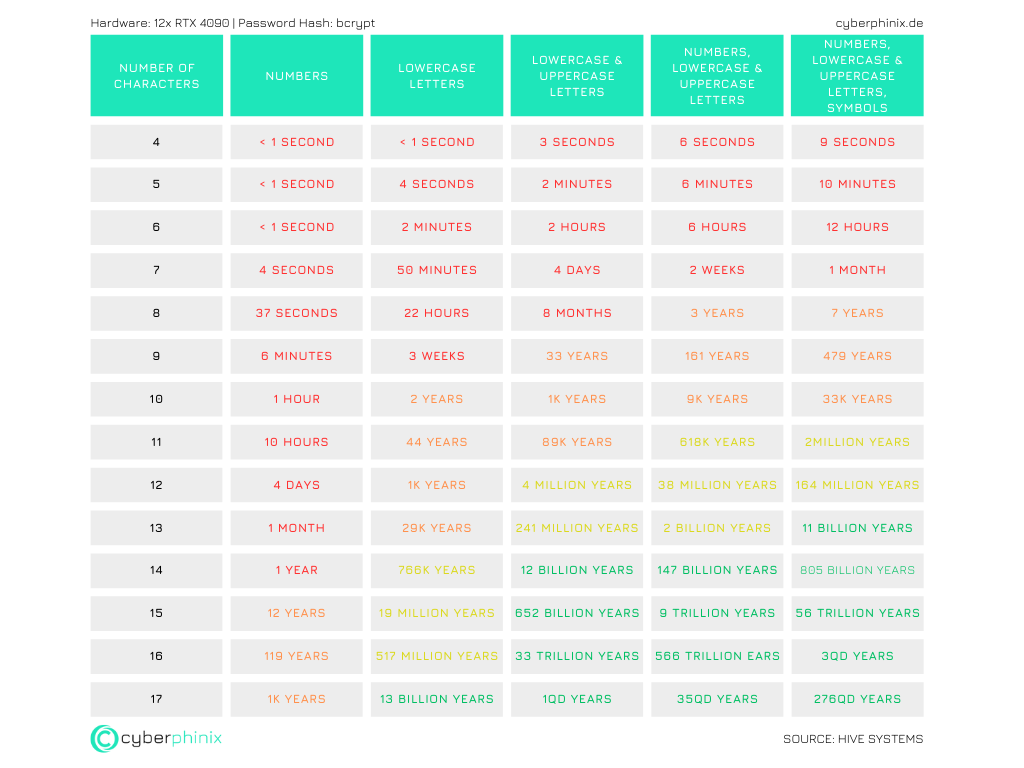
How long does it take attackers to get your password?
This question is not easy to answer. Because it depends on the use case. For example, brute forcing via a login page can take longer than guessing a password using bcrypt. The following table shows an example of how long it takes to brute force a password of a certain length for bcrypt.
Practical examples of brute force attacks
1. Simple brute force attack on a login form
An attacker sets up a script that automatically tries thousands of user name/password combinations. Here is a simple Python script as an example:
aimport requests
url = "https://example.com/login"
benutzername = "admin"
passwort_liste = ["123456", "password", "admin", "letmein", "qwerty"]
for passwort in passwort_liste:
daten = {"username": benutzername, "password": passwort}
antwort = requests.post(url, data=daten)
if "Willkommen" in antwort.text:
print(f"Erfolgreiches Login mit: {passwort}")
break2. Brute force attack on SSH
A common tool for this is Hydra:
hydra -l root -P passwortliste.txt ssh://192.168.1.13. Brute force on WPA2 WLAN passwords
Attackers use Aircrack-ng:
aircrack-ng -w passwortliste.txt -b 00:11:22:33:44:55 handshake.cap
How can you protect yourself against brute force attacks?
1. Use complex and long passwords
A secure password should be at least 16 characters long and contain random characters.
2. Activate multi-factor authentication (MFA)
Even if an attacker guesses a password, MFA helps to prevent access.
3. Account blocking after several failed attempts
Many systems block accounts for a certain period of time after several unsuccessful attempts.
4. Use CAPTCHA
A well-placed CAPTCHA can effectively stop automated attacks.
5. Change SSH ports & use Fail2Ban
sudo nano /etc/ssh/sshd_config
Port 2222
sudo apt install fail2ban6. Use honeypots
sudo apt install cowrie7. Password hashing instead of plain text storage
from bcrypt import hashpw, gensalt
passwort = "SuperSicheresPasswort!"
hashed = hashpw(passwort.encode(), gensalt())
print(hashed)
Detection & monitoring of brute force attacks
1. Log analysis
Signs of brute force attacks:
- Many failed login attempts within a short period of time
- Logins from different IP addresses to the same account
2. SIEM systems for attack detection
Security Information and Event Management (SIEM) tools such as Splunk or ELK-Stack help to detect brute force attempts.
grep "Failed password" /var/log/auth.log | wc -l3. Use of intrusion detection systems (IDS)
Tools such as Snort or Suricata can detect suspicious login attempts in real time.
Conclusion
Brute force attacks are a serious threat, but you can protect yourself and your systems with the right security measures. Use strong passwords, MFA, account locks and modern security mechanisms to thwart attackers. Security starts with you!