The Active Directory (AD) is the backbone of many company infrastructures. As a central authentication and authorization service, it plays a critical role in IT security. Secure configuration and monitoring of the Active Directory is therefore essential to ward off cyberattacks. In this article, we highlight the most important aspects of a secure AD configuration and show you the common mistakes to avoid.
Minimum access rights (Principle of Least Privilege)
Only ever grant as much access as is really necessary. Each user and each application should only have the authorizations that are required to perform their tasks.
This means more precisely:
- Create dedicated admin accounts for administrative tasks. Only use these accounts for administrative tasks and not for everyday tasks such as emails or internet research.
- Implement role-based access controls (RBAC). Define clear roles with specific authorizations and assign these roles to users.
- Restrict access of privileged groups to the absolute minimum. Regularly check access in groups such as “Domain Admins” or “Schema Admins” and remove accounts that are not required.
Secure administrative accounts
An advanced concept is the implementation of Just-in-Time (JIT) and Just-Enough-Administration (JEA). Here, administrative rights are only assigned temporarily and for specific tasks. This significantly reduces the time window in which a compromised admin account can be misused.
Regularly check all user accounts, especially those with high authorizations. Deactivate accounts that are no longer needed.
Multifactor authentication should be enabled for administrative accounts in the cloud.
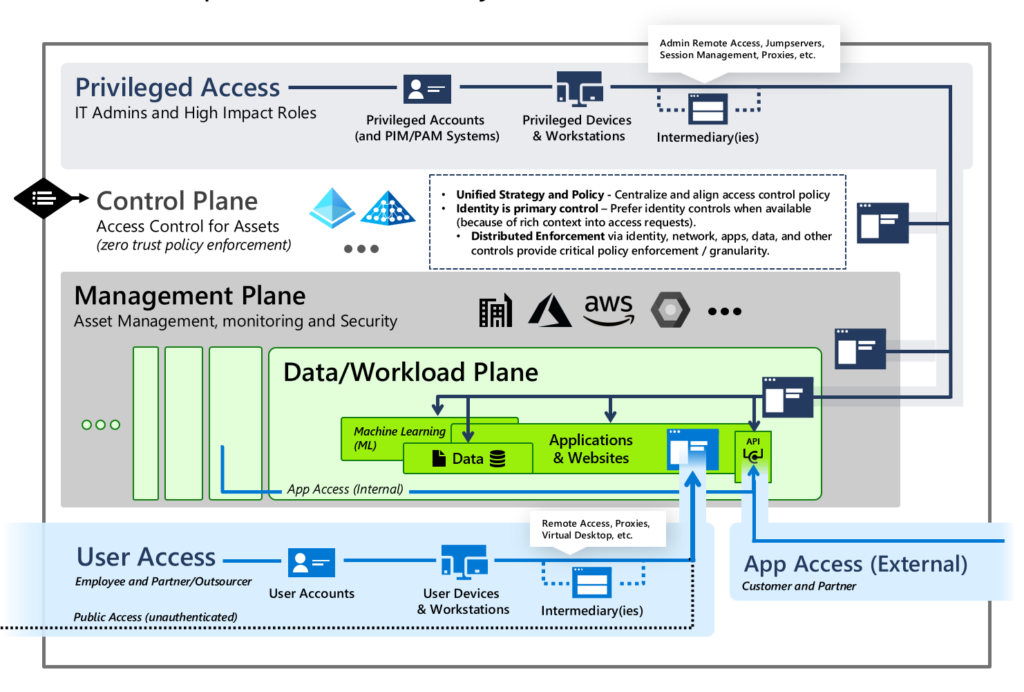
Create security areas (Enterprise Access Model)
Implement the enterprise access model (formerly also known as the tier model) for administrative access. Divide your infrastructure into different tiers (plans) with different security levels. For example, Plane 0 could include the domain controllers, Plane 1 the servers and Plane 2 the workstations. Strictly restrict access between the levels.
The implementation of this model also means that there are different accounts for each level. Accounts from Plane 2 can then no longer log in to systems from other Planes 0 and 1.
More information on the Enterprise Access model can be found on the Microsoft website: https://learn.microsoft.com/en-us/security/privileged-access-workstations/privileged-access-access-model
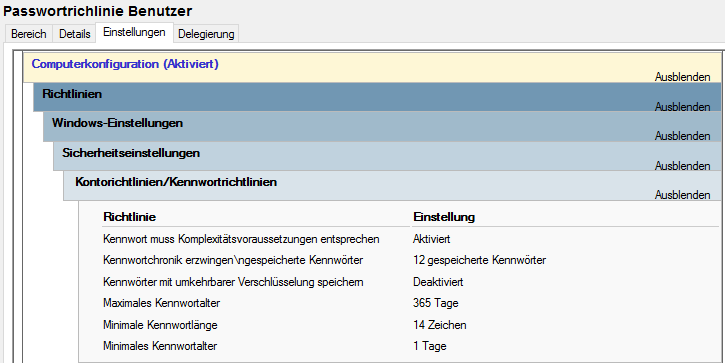
Strong passwords
Implement a strict password policy. Passwords of at least 14 characters are recommended, containing upper and lower case letters, numbers and special characters. Administrative accounts should require at least 16 characters.
You should also enforce a regular password change. However, this should not be too frequent, as this encourages users to choose insecure passwords. It is recommended to change the password once a year.
A good password policy could look like this:
Continuous monitoring
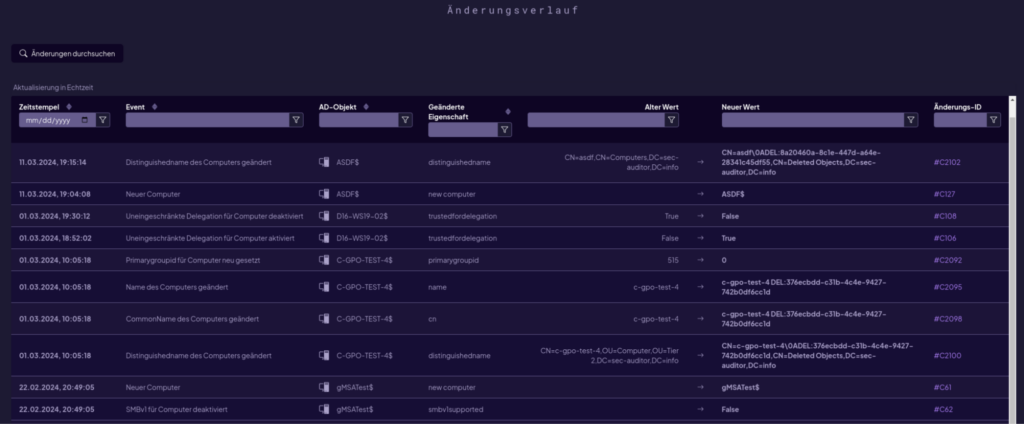
Securing the Active Directory is not a one-off operation, but a continuous process. Therefore, implement tools for real-time monitoring of security-relevant configurations. Such solutions can automatically detect and report misconfigurations before they can be exploited by attackers.
This can be implemented with SEC AUDITOR, for example. The solution continuously scans the Active Directory for vulnerabilities and misconfigurations and alerts you to potential security risks in real time. This allows you to proactively respond to threats and continuously improve Active Directory security.
You can also activate comprehensive logging of important events. Logging allows you to detect suspicious activity after the fact and perform forensic analysis of security incidents. SEC AUDITOR already logs all important events.
Backups
Test your backups and disaster recovery plans regularly. Make sure that you can restore your Active Directory quickly and reliably in the event of an emergency.
An often overlooked feature is the Active Directory recycle bin. This can be used to easily restore deleted objects. The recycle bin can be activated via PowerShell as follows
Enable-ADOptionalFeature 'Recycle Bin Feature' -Scope ForestOrConfigurationSet -Target <Name of AD-Forest>Hardening the domain controller
Only install domain controllers on dedicated servers. Avoid installing additional roles or applications on these systems.
Activate BitLocker on all drives of the domain controllers. This protects the data even if physical access to the server has been gained.
Summary
The security of the Active Directory is crucial for the overall security of a company’s IT. Careful configuration and continuous monitoring are essential to ward off cyberattacks and ensure the integrity of the system. The most important aspects of a secure AD configuration can be summarized as follows:
Minimal access rights: assign permissions according to the principle of least privilege. Use dedicated admin accounts and implement role-based access controls.
Securing administrative accounts: Rely on just-in-time and just-enough administration. Enable multi-factor authentication for cloud-based admin accounts.
Enterprise access model: Divide your infrastructure into different security levels and strictly limit access between these levels.
Strong passwords: Implement a strict password policy with at least 14 characters for normal accounts and 16 characters for administrative accounts.
Continuous monitoring: Use tools such as SEC AUDITOR for real-time monitoring and automatic detection of misconfigurations.