The ISO/SAE 21434 standard, also known as “Road Vehicles – Cybersecurity Engineering,” is an international standard developed by the International Organization for Standardization (ISO) and the Society of Automotive Engineers (SAE). Since July 2024, it has become a mandatory framework for cybersecurity management in the automotive industry. This standard provides a comprehensive set of requirements for the design and development of secure road vehicles and systems, with a particular focus on safeguarding against cyber threats.
Key points of ISO 21434
The primary objective of ISO/SAE 21434 is to ensure the cybersecurity of road vehicles by addressing potential threats posed by cyberattacks. The standard outlines best practices for the design, implementation, and management of secure vehicle systems throughout their entire life cycle. It provides comprehensive guidelines for identifying and addressing cybersecurity risks, as well as for monitoring and maintaining the security of vehicle systems. By adhering to these guidelines, organizations can effectively mitigate the risk of cyberattacks and safeguard the integrity of vehicle systems.
The key aspects of ISO 21434 can be summarized as follows:
Organizational Cyber Security Management
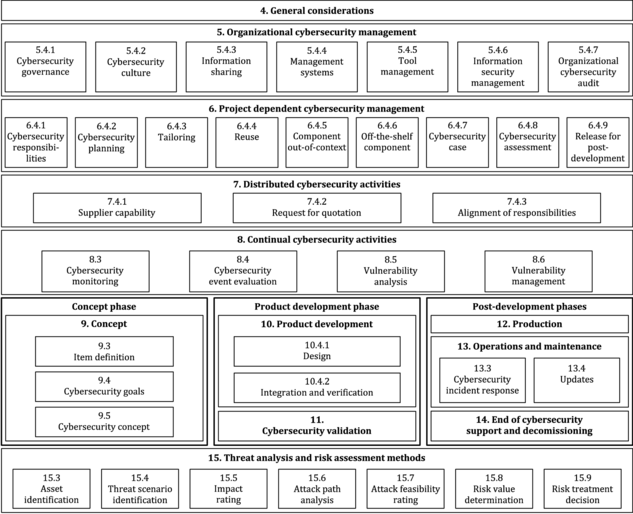
To reinforce the required Cyber Security Management System (CSMS), ISO 21434 mandates the implementation of appropriate measures at the organizational level, such as fostering a security culture and integrating security processes into the existing organizational structure. Ensuring the proper integration of the CSMS within the organization is crucial. Failure to do so can lead to challenges in executing the CSMS at the project level, resulting in avoidable costs and inefficiencies.
Project Dependent Cyber Security Management
To establish effective Cyber Security management within projects, a wide range of requirements must be fulfilled to ensure proper project oversight. This involves documenting the responsibilities of the relevant project roles and conducting thorough planning to ensure the CSMS is implemented in line with established processes. Additionally, the planning of Cyber Security assessments and the creation of a Cyber Security case—required for every release involving road approval—are essential to demonstrate the security of the control units.
Distributed Cyber Security Activities
In addition to organizational and project-specific responsibilities, Cyber Security considerations must also be integrated into sales, procurement, and resource planning. For instance, the sales department must determine the duration of Cyber Security maintenance to be offered to the OEM, which should be formalized in a contract. Similarly, procurement must ensure compliance with both cross-organizational and project-specific requirements. For example, the procurement department must secure a commitment from suppliers to provide information on vulnerabilities and weaknesses for the next 15 years. These tasks are critical and must not be overlooked. While they may seem unrelated to individual projects at first glance, neglecting them can have significant long-term consequences. For example, if suppliers stop reporting vulnerabilities after five years, this could lead to negative press coverage and damage the company’s reputation.
Continuous Cyber Security Activities
This point can be summarized as Cyber Security monitoring and vulnerability management. Companies subject to ISO 21434 should aim for continuous Cyber Security measures, as a product that is secure at a given point in time may still develop vulnerabilities over time. New vulnerabilities are discovered daily, and it is only a matter of time before they surface in any product. These issues must be addressed beyond the development phase; otherwise, the company risks legal liability in the event of incidents. In the worst-case scenario, this could be viewed as willful negligence in court, as it is irresponsible to assume 100% security. For this reason, ISO 21434 mandates ongoing product monitoring and vulnerability management.
Threat Analysis and Risk Assessment (TARA)
Threat Assessment and Risk Analysis (TARA) follows an asset-based approach, where assets and their protection requirements are identified first, followed by an evaluation of the associated risks. Based on these risks, decisions must be made regarding risk mitigation strategies—whether to avoid, reduce, share, or retain the risk—and corresponding measures must be defined. TARA is the cornerstone of the entire Cyber Security Management System (CSMS), making it essential to give special attention to this process. The more thorough and accurate the TARA, the more effective the resulting mitigation measures will be.
Concept Phase
Following the Threat Assessment and Risk Analysis (TARA), the concept phase is the most critical technical component of the Cyber Security process under ISO 21434. This phase involves defining the measures identified in the TARA. If the requirements are not clearly specified at this stage, they cannot be accurately derived, verified, or validated. The Cyber Security concept begins at the system level, and it is crucial to ensure that only system-level requirements are specified according to established principles of requirements specification. Failure to do so will hinder the testing of measures at the system level, compromising their effectiveness and increasing security risks. Additionally, this oversight affects other domains, such as software and hardware, as they will be unable to accurately derive their specific requirements. Consequently, software developers may face challenges in implementing complete solutions, leading to ineffective testing and incomplete validation of the measures.
Product Development Phase
This phase encompasses the creation of an adversarial design, as well as the development and verification/validation of the defined requirements. It is essential to make the coverage of Cyber Security requirements measurable, enabling the Cyber Security officer to assess the effectiveness of the measures when preparing their security certificate. The success of this phase is highly dependent on the quality of the requirements specification; the more precise and comprehensive the requirements, the more effective the development process and the resulting security outcomes will be.
Post-Development Phase
In the post-development phase, it is crucial to establish procedures for handling security incidents. Often, the project team is disbanded at this stage, leaving no designated personnel to address potential incidents. Therefore, the company must define appropriate procedures to ensure an effective incident response.
In addition to incident management, production efficiency is vital. In the automotive industry, even a single second of delay can cost up to €10,000, while saving just one second can significantly boost profitability. During production, Cyber Security measures must be implemented, such as injecting key material into control units and configuring settings (e.g., disabling JTAG).
Addressing the decommissioning of an ECU is also essential. It is important to determine whether personal data needs to be erased and if any information could potentially jeopardize the security of an entire fleet if exposed.
A more precise representation of ISO 21434
Given that the V-model is mandatory in the automotive industry for ASPICE compliance, I have used this diagram to realistically represent the various sections of ISO 21434. The Cyber Security management tasks at the organizational level are overarching and apply to all projects, reflecting their practical implementation. These tasks are positioned at the top of the diagram. Project-specific Cyber Security management tasks and monitoring/vulnerability management extend throughout the entire project duration and beyond, so they are depicted on the right side, running parallel to the project-related activities. Project-specific tasks are listed on the left, arranged sequentially in the appropriate order.
Problem with ISO 21434
The standard is often criticized for being too vague and leaving considerable room for interpretation, which can be exploited. The interpretation of the standard depends on the individual responsible, their level of expertise, and their objectives. This variability can lead to a checkbox mentality, potentially compromising the quality of the security process. A more precise specification would be preferable to ensure consistent quality and security across the automotive industry. Currently, each company interprets and implements the standard based on the understanding of those in charge, which may not always yield optimal results.
Practical Implementation of ISO/SAE 21434: Challenges and Solutions
Implementing ISO/SAE 21434 is not just about compliance – it requires a deep transformation of existing processes, structures, and responsibilities. This chapter provides practical insights into how organizations can effectively integrate the standard’s requirements into their daily operations.
1. Integration into Existing Processes
The standard demands that cybersecurity considerations be embedded across the entire product lifecycle – from concept and development to production, operation, and decommissioning.
Common measures include:
- Extending development models (e.g., V-model, Agile) with security activities
- Enhancing existing requirements management systems with cybersecurity elements
- Embedding cybersecurity checkpoints into milestone gates and project reviews
2. Roles, Responsibilities, and Awareness
ISO/SAE 21434 emphasizes the importance of clearly defined roles and responsibilities. Organizations must establish dedicated functions and raise awareness across teams.
Typical approaches:
- Appointing cybersecurity leads at project and organizational levels
- Providing targeted training for development, purchasing, quality, and compliance teams
- Promoting a culture of security that encourages risk transparency and documentation
3. Risk-Based Approach
At the heart of the standard is a risk-oriented mindset. Security goals are derived from the analysis of potential threats and vulnerabilities.
Key actions include:
- Performing Threat and Risk Assessments (TARA)
- Evaluating risks at both component and system levels
- Documenting security goals, mitigations, and their effectiveness
4. Tool Support and Documentation
Comprehensive documentation is a core requirement of ISO/SAE 21434. Without the right tools, managing traceability and version control becomes inefficient.
Recommended practices:
- Leveraging Application Lifecycle Management (ALM) tools with integrated security features
- Using standardized security case templates for consistency
- Ensuring traceability between risks, requirements, and mitigations
5. Collaboration with Partners and Suppliers
Cybersecurity in the automotive domain is a system-wide concern. The standard requires organizations to involve their supply chain – especially in defining and verifying security requirements.
Best practices:
- Including cybersecurity requirements in supplier agreements
- Conducting joint risk analyses and interface assessments
- Establishing security sign-offs as part of quality assurance processes
Conclusion
In conclusion, ISO 21434 sets a critical standard for Cyber Security in the automotive industry, requiring a comprehensive approach to ensure the protection of road vehicles against cyber threats. The standard emphasizes the importance of integrating Cyber Security measures across organizational, project-specific, and post-development phases. This includes establishing robust Cyber Security Management Systems (CSMS), conducting thorough Threat Assessment and Risk Analysis (TARA), and ensuring continuous monitoring and vulnerability management.
The concept phase is particularly pivotal, as it involves defining and implementing measures based on the TARA. The quality of these measures depends heavily on the precision of the requirements specification. Additionally, the post-development phase must address effective incident response and production efficiency, while also considering the secure decommissioning of Electronic Control Units (ECUs).
Despite its importance, ISO 21434 is sometimes criticized for being vague and open to interpretation, which can lead to inconsistent implementation and a checkbox mentality. A more detailed specification would help ensure uniform quality and safety across the industry, preventing potential compromises and inefficiencies.
Overall, adherence to ISO 21434 requires meticulous planning and execution at every stage, from initial design to post-production. By addressing these aspects diligently, companies can better safeguard their systems and maintain robust Cyber Security standards in an increasingly complex and vulnerable landscape.