The EU NIS2 Directive is a decisive milestone for cybersecurity in Europe. Since its announcement at the end of 2022, an estimated 30,000 to 40,000 companies in Germany alone will be faced with the challenge of fulfilling the new requirements. The directive aims to establish uniform security standards throughout the European Economic Area and significantly strengthen the resilience of network and information systems. The EU member states must transpose this directive into national law by 17 October 2024. In Germany, this is being done through the NIS2 Implementation and Cyber Security Strengthening Act (NIS2UmsuCG).
If companies are located in critical sectors such as energy, health and digital infrastructure, the NIS2 Directive must be applied. However, there are other criteria that are aimed at affecting many more organizations. These include having more than 50 employees and an annual turnover or balance sheet total of more than 10 million euros. Smaller companies can also be affected if they play a significant role in critical infrastructures or carry out particularly risky activities. These criteria ensure that the NIS2 Directive is applied specifically to companies that play an important role in society and the economy.
This mainly applies to so-called ‘essential’ and ‘important’ organizations that are active in critical sectors such as energy, health, transport and digital infrastructure. Small and medium-sized enterprises (SMEs) are generally exempt from NIS2 unless they play a key role in these sectors or carry out particularly risky activities. Companies that do not fall into these categories and do not operate critical infrastructure are therefore not obliged to fulfil the NIS2 requirements. The exact categorisation is carried out at national level to ensure targeted implementation.
Table of Content
What does NIS2 require?
The NIS2 Directive requires the companies concerned to introduce ‘appropriate and proportionate technical, operational and organizational measures’. These measures should help to manage security risks to network or information systems and minimize the impact of security incidents. Several factors must be considered, including the state of the art, European standards, the cost of implementation and the existing risk.
Article 21(2) of the NIS2 Directive specifies the minimum areas that these measures must cover:
- Risk analysis and security concepts: Companies must carry out systematic analyses of their IT risks and develop appropriate security concepts.
- Management of security incidents: Measures and plans for responding to security incidents must be in place to ensure fast and efficient responses.
- Business continuity: Business continuity strategies such as backup, recovery and crisis management must be implemented.
- Supply chain security: The entire supply chain, including security requirements for third-party providers, must be taken into account.
- Security measures for the acquisition, development and maintenance of information systems: This includes vulnerability management and disclosure.
- Assessing the effectiveness of risk management: Companies must continuously review whether their risk management measures are effective.
- Cyber hygiene and cyber security training: Training and cybersecurity awareness among employees is essential.
- Cryptography and encryption: The use of encryption technologies to secure sensitive data is required.
- Staff security, access control and asset management: This includes multi-factor authentication and secure means of communication.
Legal and economic implications of NIS2
The NIS2 Directive has significant legal consequences for companies that do not fulfil the requirements. EU member states are obliged to impose strict sanctions for violations of the directive. These sanctions can range from substantial fines to restrictions on business operations. It is therefore essential that companies begin implementation at an early stage in order to avoid legal consequences.
There are severe fines and penalties for companies that fail to comply. Companies can be fined up to €10 million or 2% of their global annual turnover, whichever is higher. These penalties are intended to ensure that companies take the necessary cybersecurity measures seriously. In addition to financial penalties, other sanctions such as operating restrictions or increased supervisory measures can also be imposed. This emphasizes the urgency and importance of complying with the NIS2 requirements.
The NIS2 Directive also offers economic advantages. Companies that implement the directive at an early stage can use this as a competitive advantage. A robust security management system signals to potential customers and business partners that the company takes the security of its IT systems seriously, which creates trust and can lead to a stronger market position in the long term.
Practical examples and best practices
One example of the successful implementation of cyber security requirements is Deutsche Telekom, which implemented extensive measures to secure its IT systems and train its employees at an early stage. This commitment to cyber security has not only helped to strengthen the company’s resilience, but has also increased customer confidence.
Another example is the automotive industry, where companies such as Volkswagen and BMW have paid increased attention to the security of their supply chains in recent years. By introducing strict security guidelines for their suppliers, these companies have been able to significantly reduce the risks in their supply chain and better prepare themselves for potential attacks.
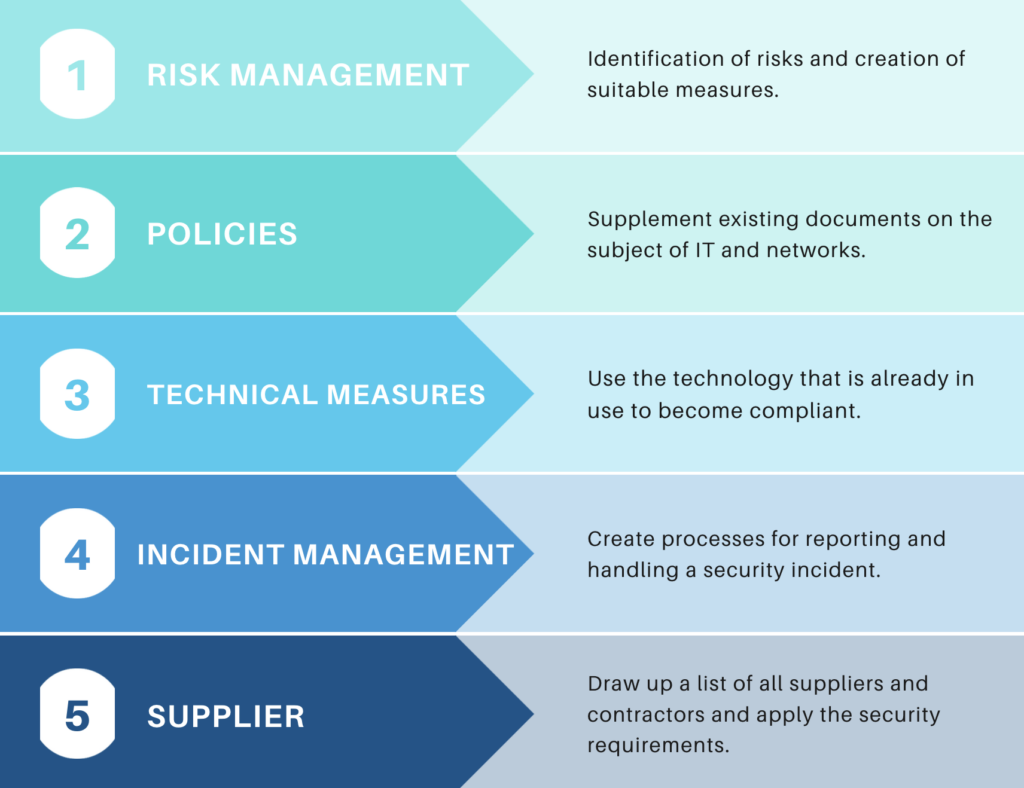
Key factors for the implementation of NIS2
Several key factors are decisive for the successful implementation of the NIS2 directive.
Many of these elements may already be in place in your organization, providing a solid foundation for NIS2 compliance:
- Existing risk management processes: Organizations that already have a robust risk management system in place can use this as a basis and adapt it to the specific requirements of NIS2.
- IT security policies and processes: Existing IT security policies can be extended to meet the new requirements of NIS2. This also includes the adaptation of training programmes for employees.
- Technical security measures: Existing technologies such as firewalls, intrusion detection systems (IDS) and encryption solutions should be reviewed and, if necessary, expanded to meet the increased security requirements.
- Incident response strategies: organizations that already have contingency plans and processes in place to deal with security incidents should review these and ensure that they meet the requirements of NIS2.
- Supplier management: The NIS2 directive places great emphasis on supply chain security. Companies should review existing supplier contracts and relationships regarding security requirements and adapt them if necessary.
Expert tips and further resources
Security experts emphasize that implementing the NIS2 directive should not be seen as a one-off task, but as an ongoing process. Cyber security is not a goal that can be achieved and then ticked off – it is a constant process of adaptation and improvement. Organizations should therefore regularly review and adapt their security strategies to keep pace with constantly evolving threats.
For further information and detailed guidance on implementing the NIS2 directive, organizations can refer to resources such as the NIS Collaboration Group. This report provides valuable insights and practical tips for implementing the necessary security measures.
Technical measures in detail
A key component of the NIS2 directive is the technical protection of IT systems. This includes the implementation of multi-factor authentication (MFA) to prevent unauthorised access. The installation of intrusion detection systems (IDS) enables companies to recognise potential attacks at an early stage and take appropriate countermeasures.
Another important element is the encryption of sensitive data. By using modern encryption technologies, companies can ensure that even in the event of data theft, the information is not easily accessible. These technical measures should be supplemented by regular security checks and penetration tests to ensure that they work effectively and are state of the art.
Summary
The NIS2 directive represents a significant challenge, but also an opportunity for organizations to update their cyber security strategies. With careful planning and the utilization of existing resources, companies can implement the requirements of NIS2 efficiently and effectively. It is important that the process of implementation is not just seen as a one-off measure, but as a continuous improvement process to ensure high security standards in the long term.
By viewing compliance with these standards not just as a legal obligation, but as an integral part of the corporate strategy, companies can not only minimize risks, but also strengthen the trust of their customers and partners in the long term.