
What is BSI IT baseline protection?
The IT-Grundschutz BSI is a framework developed by the German Federal Office for Information Security (BSI) to ensure information security in companies and public institutions. It offers a comprehensive methodology for identifying and dealing with security risks and implementing suitable IT security measures. IT baseline protection helps organizations to raise their IT systems and processes to a high level of security while at the same time meeting legal and regulatory requirements.
Key components of the IT-Grundschutz Compendium
Process building blocks and system building blocks are central elements in the IT-Grundschutz Compendium. While process building blocks are dedicated to general organizational and security management topics, system building blocks focus on specific IT systems and technologies.
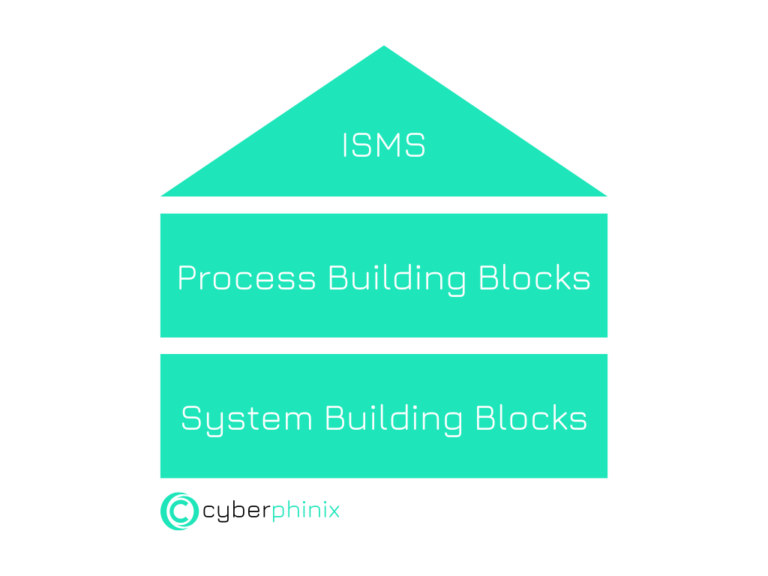
Process Building Blocks
Examples of process modules are
- ISMS: Describes how a holistic security management system can be set up and operated.
- Operation: Includes all aspects required to maintain the secure operation of information systems.
System Building Blocks
System modules address specific technologies, for example:
- Servers: Measures and requirements for the protection of servers.
- Clients under Windows: Security approaches for desktop systems.

Breakdown of the BSI standards
1. BSI Standard 200-1
- Content: General requirements for an information security management system (ISMS). Compatible with ISO 27001, based on ISO 27002.
2. BSI Standard 200-2
- Content: Basis for the implementation of an ISMS in accordance with IT-Grundschutz. Establishes new procedures for implementation and uses the structure of 200-1.
3. BSI standard 200-3
- Content: Bundles all risk-related steps of the IT-Grundschutz methodology. Reduces the effort for the risk analysis after the IT-Grundschutz analysis.
4. BSI Standard 200-4
- Content: Instructions for implementing a Business Continuity Management System (BCMS).
5. Guide to basic protection according to IT-Grundschutz
- Content: Compact guide for small and medium-sized enterprises and public authorities on setting up an ISMS.
6. Guide to the migration of security concepts
- Content: Assistance for the migration from old IT-Grundschutz methods to the modernized IT-Grundschutz.

Key elements for information security
The key elements for information security according to IT-Grundschutz include the assessment and treatment of security risks, the protection of sensitive data and ensuring the integrity and availability of IT systems. The risk-based approach and continuous improvement of the security level are fundamental to this.
A clear example to illustrate security measures is the securing of server rooms:
- Access controls prevent unauthorized access.
- Fire protection equipment and air conditioning protect against physical hazards.
- Logging and monitoring ensure the traceability of actions.
The combined use of these methods from different components of IT baseline protection creates a comprehensive security concept that efficiently reduces risks.
Creation of an information security management system (ISMS)
The establishment of an information security management system (ISMS) is a central component of BSI IT-Grundschutz. An ISMS comprises a systematic approach to managing and continuously improving the security of information in an organization. Three aspects in particular are taken into account: Confidentiality, integrity and availability of data.
Steps for implementing an ISMS:
- Determine the scope: Clearly define which data, systems and processes the ISMS should cover.
- Establish information security policies: Establish your organization’s basic security objectives and policies.
- Risk management: Carry out a risk analysis to identify and assess potential security risks.
- Implement security measures: Based on the risk analysis, implement appropriate security mechanisms to mitigate or eliminate identified risks.
- Documentation and training: Document the ISMS comprehensively and train employees to raise security awareness.
- Monitoring and improvement: Regularly monitor the effectiveness of the ISMS and make adjustments to enable continuous improvement.

Risk analysis and management as part of IT baseline protection
Risk analysis and management in the context of IT baseline protectionRisk management is an essential process in the context of IT baseline protection and serves to identify, assess and manage potential risks to information security.
A pragmatic approach to risk analysis involves the following steps:
- Identification of security risks: Record all potential threats and vulnerabilities that could compromise the security of your information.
- Risk assessment: Assess the likelihood of a risk occurring and its potential impact.
- Prioritization: Rank the risks according to their importance and urgency.
- Deriving measures: Determine suitable security measures to address critical risks.
Continuously reviewing and updating the risk analysis ensures that new and changing risks are identified and addressed in good time.

Importance of regular updates and adjustments
The world of information technology and cyber security is changing rapidly. New technologies, threat landscapes and business practices require continuous adaptation and updating of IT baseline protection and the underlying ISMS. Regular reviews and adjustments to the ISMS and security measures ensure that your organization remains resilient to new security threats while ensuring compliance with legal and regulatory requirements.
Examples of reasons for review and adjustment:
- Introduction of new IT systems or technologies
- Changes in the organizational structure
- Updates to legal or industry-specific security requirements
- Findings from security incidents or audits
Schedule regular reviews and plan resources for updating the ISMS and the IT security strategy. This ensures that the protection of your information and IT resources remains at a permanently high level.

ISO 27001 certification based on IT baseline protection
ISO 27001 certification is an internationally recognized standard for information security management systems (ISMS). For companies that have implemented the BSI’s IT baseline protection, the path to ISO 27001 certification is the logical next step. ISO 27001 certification on the basis of IT-Grundschutz makes it possible to confirm an already high level of security and to have this formally recognized internationally.
The path to ISO 27001 certification:
- Initiation and planning: First, the company must decide on certification and clarify resources and responsibilities.
- ISMS implementation: Based on the IT baseline protection, which already covers most of the requirements of ISO 27001, the ISMS is adapted and documented in accordance with the specific requirements of ISO 27001.
- Internal audit: Before the actual certification, an internal audit is carried out to ensure that all processes and documentation meet the requirements.
- Management review: The management reviews the ISMS in terms of its effectiveness and appropriateness.
- Certification audit: An external auditor reviews the ISMS and decides whether certification can be granted.

Connection and differences between ISO 27001 and BSI IT-Grundschutz
The IT-Grundschutz BSI provides practical guidance for implementing a comprehensive information security concept. It is particularly widespread and recognized in German-speaking countries. ISO 27001 sets an international standard that defines the requirements for an ISMS.
Connection:
IT-Grundschutz provides concrete measures and control mechanisms that are essential for achieving the ISO 27001 requirements. Certification based on IT baseline protection already provides a solid foundation that only needs to be supplemented with specific ISO 27001 requirements.
Differences:
The biggest difference is the level of detail and the geographical spread. While IT-Grundschutz prescribes very detailed measures and security controls, ISO 27001 focuses more on the management system and is internationally recognized.

Benefits of certification for organizations and companies
ISO 27001 certification based on IT baseline protection offers numerous advantages:
- International recognition: ISO 27001 certification is recognized worldwide and signals a serious commitment to information security to external partners.
- Competitive advantage: Especially in tenders and with customers, certification can represent a decisive competitive advantage.
- Risk minimization: Certification reduces the risk of security incidents through the systematic identification, assessment and treatment of risks.
- Increased efficiency: The implementation of an ISMS leads to more efficient and structured processes in the area of information security.
Examples of the benefits of certification include companies that have not only optimized their internal processes through the implementation of an ISMS and subsequent certification, but have also been able to strengthen the trust of their customers. Banks, insurance companies and IT service providers, for example, are sectors in which certification is almost considered standard and contributes significantly to business security.







